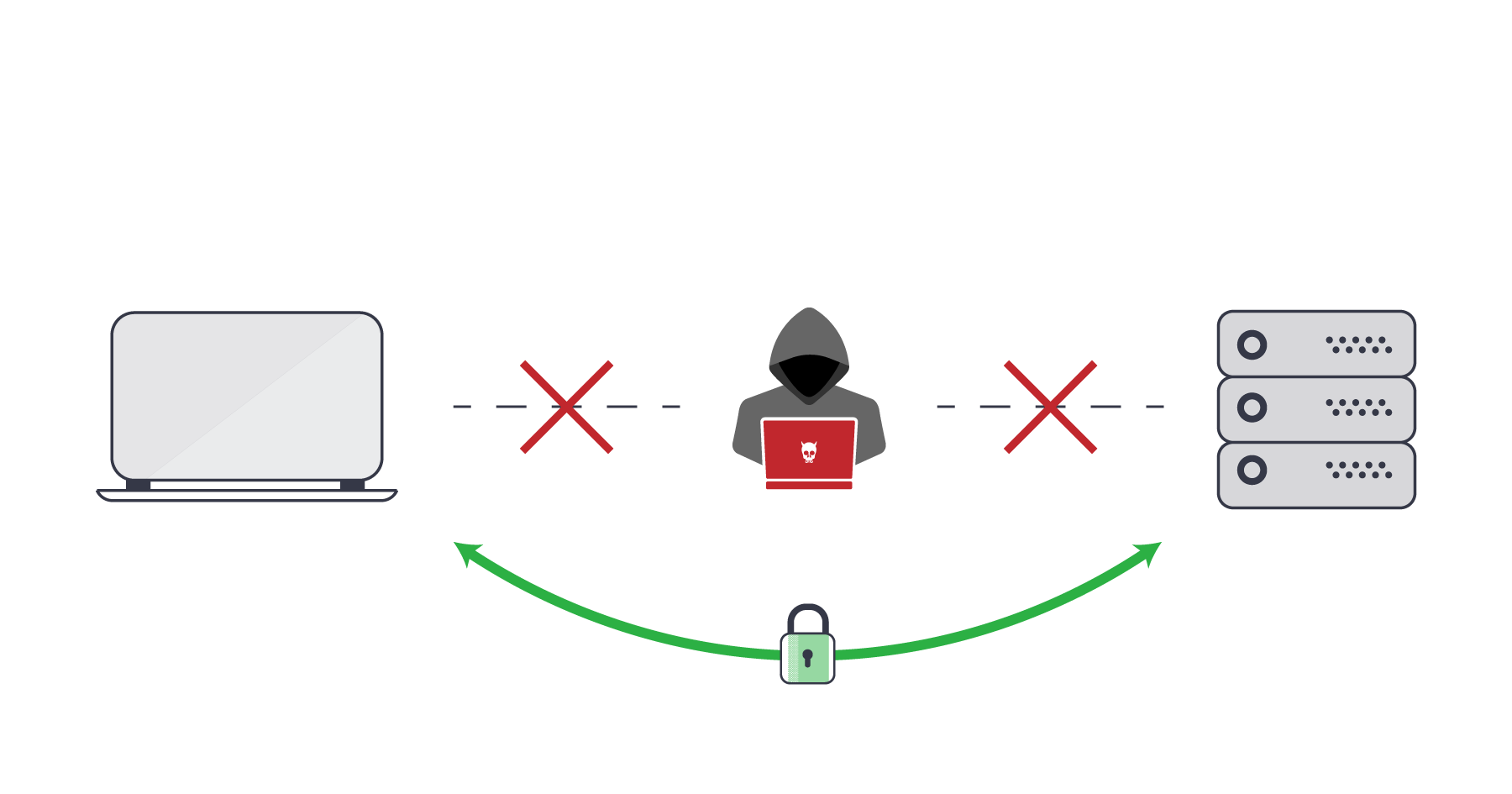
Hardware cryptocurrency wallets are believed to be the most secure way to safeguard your digital assets.
However, several reports have popped up on the internet in the recent past that display how hardware wallets are vulnerable to man-in-the-middle attacks or MITMs.
As a result, crypto investors are concerned about whether they should stop using a hardware wallet.
If not, then how can attacks like MITM be prevented?
In case you are curious about it too and wondering what a “man in the middle” attack is and how it can be prevented, then here is everything you need to know:
What is a Man-in-the-Middle (MITM) Attack?
In layman’s terms, imagine you are sending a letter to your friend.
However, instead of the note going to your friend directly, someone else in the middle accesses it, reads what’s written inside, and sends it further to your friend without you knowing.
Also, there is a possibility that the middle person has changed something inside the letter.
Well, this is what a Man-in-the-Middle attack looks like.
In other words, a Man-in-the-Middle attack is a cyber-attack where hackers alter the communication between two parties or you and your hardware wallet.
Imagine you are trying to send cryptocurrencies from your hardware wallet somewhere else.
But since a hacker is sitting in the middle, they can alter the receiver addresses, and your funds will get deposited in the hacker’s wallet instead of the actual receiver.
New to crypto investing? Know What is a watch-only address in a crypto wallet?
How MITM Attacks Work on Hardware Wallets?
We all know that hardware wallets are designed to provide an additional layer of security to crypto users by storing their private keys in an offline environment.
Unfortunately, hardware wallets are not immune to Man-in-the-Middle attacks.
As a result, most fraud occurs during the transaction signing process.
When users try to send crypto from their hardware wallet, they usually have to connect it to a device like a PC or phone.
But if the phone or computer is compromised, the hacker can easily manipulate the transaction details, such as the receiver addresses or the amount you are sending.
Furthermore, the hacker can display fraudulent messages on the device screen to trick the user into confirming a transaction.
Examples of MITM Attacks
A hacker can interfere with the communication between your hardware wallet and your computer or smartphone in several ways.
Some common examples are:
- Transaction Tampering:
The most common method is transaction tampering.
This usually happens when you try to send Bitcoin to some crypto exchange or your friend.
You start by plugging your hardware wallet into your computer, entering the receiver address, and confirming the transaction.
However, if a hacker manages to interfere in this process without you knowing, they can easily alter the receiver address.
So, instead of the actual receiver getting the funds, the hacker gets it.
- Fake Wallet Interface:
Another common method is a fake wallet interface.
In this case, you usually get to see a fake application or a compromised computer screen that looks exactly like the interface of your hardware wallet.
So, when you enter your transaction details while completing a transaction, you are giving away your private keys to the hacker.
As a result, your wallet gets compromised.
The best way to prevent yourself from falling for these tricks is to download software from the official websites.
Intercepting Updates:
Another attack is intercepting updates.
The hackers can conduct a Man-in-the-Middle attack during a firmware update.
The hacker might trick you into downloading a fake security or firmware version for your hardware wallet.
However, the firmware update comes with malware embedded.
As a result, the hacker can later use the malware to compromise your wallet, monitor your transactions, and even take full control of the hardware wallet and funds.
Recommended Read: Why have multiple accounts on multiple crypto exchanges?
How do you Detect a Man-in-the-Middle Attack in Hardware Wallets?
Detecting an MITM attack as early as possible is crucial.
If someone sneaks into your activities, it could lead to a huge financial risk.
To detect these sorts of attacks, here are some insights you can follow:
- Unexpected Prompts:
After plugging your hardware wallet into your device, if you notice that your wallet is asking for certain information that it never asked for, there might be something suspicious.
To verify this, you can run the message on Google to verify the genuineness of it.
Alternatively, your wallet may also throw random prompts on your screen.
So, in such a case, you should instantly unplug your hardware wallet and dig deep into what’s happening.
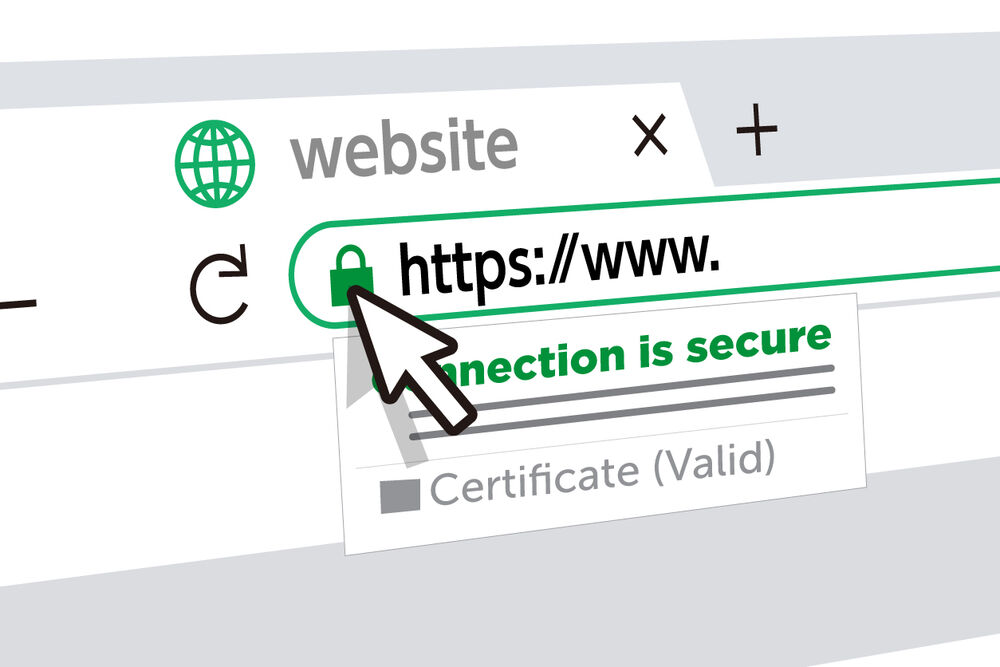
- Check for SSL/TLS Certificates:
Most hardware wallets come with a desktop or phone-based app.
However, certain hardware wallets have a web interface; if you use it, take extra precautions.
While accessing any wallet-related services online, ensure you are visiting the official website only and not any fake ones.
Also, ensure it has SSL/TLS certificates, which can easily be verified by looking at the green padlock on the site URL.
If it doesn’t have proper SSL certifications, you mustn’t enter your confidential details.
- Latency in Transactions:
You should also check if your connections are occurring in real-time or taking longer than usual.
However, it could be an internet issue, too.
But if your internet works just fine and your transactions take slightly longer than usual, there is a high chance that your transactions or the network will be routed through the hacker’s system.
- Monitor for Phishing:
Phishing is another major method that hackers use to fool users.
Hence, you must pay extra attention to any crypto-related emails or messages that you get.
Always verify the sender’s email address and see if it’s from the official website only.
Also, make sure to take extra precautions while clicking on suspicious links.
- Use Security Software:
Security software can also be installed on your PC to stay extra protected.
Security software like anti-virus can often detect malware Trojans and even sometimes can detect any potential MITM attacks.
As a result, you can take necessary actions.
- Network Tools:
The final step is to use network tools.
Several tools allow you to see if any suspicious activities are going on in your network.
However, this will require technical knowledge of how the network works.
But definitely, it is not too complicated to learn.
Recommended Read: What is OTC trading in crypto?
Prevention and Defense Mechanisms
As a hardware wallet user, you must take specific steps to prevent MITM attacks.
These steps include:
- Always Verify:
Always double-check the recipient’s address when sending a huge amount of crypto.
If you spot something fishy, do not proceed.
- Secure Connections:
Always connect your hardware wallet to a computer or smartphone you completely trust.
Make sure that the device is not infected with viruses or malware.
This will eliminate the risk of any spoofing and MITM attacks.
- Keep It Updated:
You should also regularly update your hardware wallet’s firmware, antivirus program, and device OS.
However, ensure you complete the updates through the official verified channels only.
If you download wallet firmware from suspicious sites, it can lead to a wallet-compromised situation.
- Use Trusted Networks:
Only use trusted networks, plus avoid using public Wi-Fi when managing your cryptocurrencies with your hardware wallet.
Public Wi-Fi is one of the main spots where hackers always spoof around users to steal confidential information.
If you must use public Wi-Fi, use a VPN to secure your connection.
- Two-Factor Authentication (2FA):
Always use 2FA to add an extra layer of security.
2FA will require multiple authentications while logging into your hardware wallet or completing your transaction.
So, even if the hacker gets access to your wallet, they will still need access to your 2FA code.
So, any unwanted hack attempts can be prevented.
- Educate Yourself:
Last but not least is to stay informed about the latest security threats and how to avoid them.
You can follow some security magazines or update yourself with the latest cryptocurrency news.
So whenever there is a new vulnerability around crypto wallets or exchanges, you can take the necessary steps to prevent any attacks coming your way.
Recommended Read: What to do if your crypto exchange account gets hacked?
Conclusion
That was an overview of the Man-in-the-Middle attacks on hardware wallets and how to prevent them.
The key here is always to be suspicious about your activities and ensure that the device and the connection you are using are safe whenever you are making a transaction.
Avoid clicking on suspicious links to complete transactions.
Plus, make sure to keep your seed phrase protected.
If a hacker gets access to that, they can easily compromise your wallet.
If you transfer crypto daily, you can use a separate wallet for the job with only that amount of funds you can bear the loss of.